Introducing the Insider Attack Matrix
- Information Security
There’s something undeniably attractive, yet archaic, about the idea of walls. Hadrian ordered his built, bisecting Britain, in AD 122. The idea of keeping the baddies at bay on the opposite side, can be highly appealing in a simplistic sort of way. It’s an age-old metaphor for conceptualising conflict.
Much of the literature, research and work in modern digital security follows this concept – keep the threats external, outside, separate from what must be safe and secure. It focuses on technical attacks from external actors, such as hackers, organised crime, un-friendly nation-states, and Advanced Persistent Threats (APTs). Tools such as the Lockheed Martin Cyber Kill Chain or the MITRE ATT&CK frameworks are very useful in this context.
While the majority of our industry moves unrelentingly forward with the external threat as a priority, we’ve been thinking about something slightly different. What if the attacker never needed to breach your walls in the first place? What if they were already inside?
The insider threat, despite being a real and present danger, is often not given the same attention as external threats. Companies that suffer insider attacks often try to settle them in-house – by firing the staff – to avoid a lengthy public trial. The effect of organisations remaining tight-lipped about having suffered insider attacks leaves it up to security professionals to hypothesise what an insider theoretically could do.
Consequently, no systematic, methodical analysis of TTPs (Tactics, Techniques and Procedures) of internal threats by privileged insiders has been executed to date. The danger from disgruntled employees, aggrieved contractors or ill-intentioned business associates is waiting to be analysed.
This may be because there are no easy answers, ready to be shrink-wrapped and sold as a “solution suite” or as an ongoing subscription. Even the consulting contracts are often bespoke, tailored to the individual organisation and its particular peculiarities. One-offs don’t often make for compelling opportunities to scale.
However, we believe it’s time to elevate understanding of insider threat – and a burgeoning expert community has coalesced around this same conclusion. It has produced a fair amount of research and several very good reports, many of which we consulted. We welcome any additional information or collaborative opportunities on this topic.
G-Research makes money not by selling software or offering security consulting. We’re one of Europe’s leading quantitative finance research firms. We have valuable intellectual property and take the concept of the insider threat very seriously.
We present this analysis as a first step in building the better understanding of those threats.
Methodology
Any analysis of threats must begin by collecting and analysing data and anecdotes about historical attacks. This has produced an abundance of research and several very good reports, many of which we consulted. But there’s a paucity of actionable information coming from the analysis of the size and scope of digital attacks perpetrated by insiders. This may be due to the sensitive nature of such disclosures, or to the fear that vulnerabilities, once discussed, will illustrate a systemic weakness that may be later exploited. This is different from the danger from external threats, which though are also considered ever-present, are not necessarily due to inherent or organisational-genetic weaknesses that may later be exploited.
We took as a starting point, the CERT Guide to Insider Threats, an authoritative text by Andrew L. Moore, Dawn Cappelli, and Randall Trzeciak. We saw many patterns in it that mirrored the methodology and syntax of both the Lockheed Martin Cyber Kill Chain and the MITRE ATT&CK frameworks. It seemed natural to begin grouping and classifying the examples CERT had identified with the attack techniques and styles Lockheed and MITRE had teased out.
As we were going through the case studies, we became more aware of the problem ourselves. We started noticing news articles, magazine stories, and even movie scenes where trusted insiders were causing trouble for their organisations, either by accident or due to ill-intention. We expanded our consideration to eventually encompass some 50 separate, well-documented incidents.
We decided to focus on ‘real world’ examples of things that had actually happened. Reality can be stranger than fiction, and many of the cases we considered were bizarre enough in their own right. We wanted everything to be realistic, much like the MITRE ATT&CK Framework.
Of course, no examination of the insider threat may ever be considered complete. The landscape is continuously evolving as new techniques and technologies take hold. We welcome input and assistance to better develop our methodology and understanding of the issue.
Findings – The Kill Chain
We found that much like external threat actors, the progression of an insider attack through its various phases seems consistent across case studies. Starting with the excellent insider threat kill chain produced by Patrick Reidy, we have expanded it to cover more of the lifecycle of an insider attack.
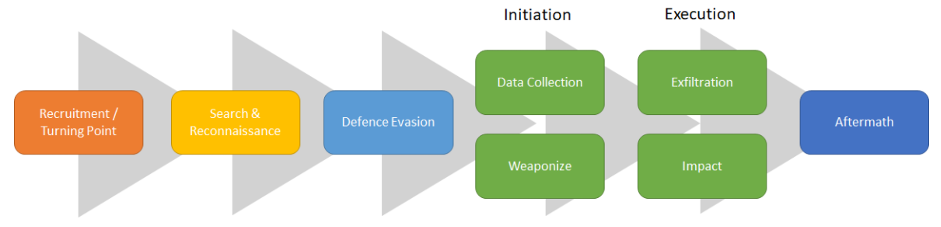
Figure 1: Insider Killchain
Recruitment/Turning Point
Attackers might be malicious from the start or a major event might turn an insider bad. This is an often-neglected area of focus, but identifying these events can allow you to pre-empt the actions of high-risk members of staff. While also providing greater assurance around the authenticity of other possible alerts produced further down the kill chain.
Search/Reconnaissance
Often insiders know what data/accesses are valuable to them, but they don’t know where the data are, or are not in a position to access/exploit them. When an insider doesn’t know what they are after they could be searching for any opportunity. This search and reconnaissance stage can provide some unique early warnings, as well as provide additional assurance when these alerts are linked with other alerts that might otherwise be considered false positives.
Defence Evasion
By trying to hide what they are doing, an insider is making a statement that their actions are malicious. This action by itself might be all that is needed to start an investigation into a suspected malicious insider.
Initiation
Initiation is the first point the attacker does something that could damage the company. Here we describe it as either data collection or weaponising a malicious attack.
Data Collection
Amassing data could be malicious and unauthorised (to steal from the company) or legitimate and approved as part of a person’s roles and responsibilities within the company, for example, knowledge management. There are also a range of different manual and technical methods to obtain and collect data.
Weaponise
This involves the staging and initiation of a malicious attack either through technical means, such as installing malware or enterprise business process means, e.g., making work requests of other teams disguising an actor’s malicious intent.
Execution
Execution is the point of the Insider Kill Chain most companies focus on, through using Data Loss Prevention (DLP) protection, detection controls around fraudulent transactions, backup and resilience processes and incident response plans.
Exfiltration
Exfiltration is exactly what it says on the tin. Here the TTPs list all the different ways to get stolen data from within the company’s premises/network to an external location out of the company’s control.
Impact
Impact is the effect of an attack after it has succeeded. The attacker has succeeded in hurting the company in a way that is noticeable (taken down servers, publicly exposed the company or extorted the company) or in ways that are not noticeable but could be detected (e.g., transferring money, malicious changes/deletion of data).
Aftermath
Although an attacker at this stage has probably already succeeded at exploiting the company, you still want to be able to know when you have been compromised. The ability to remediate, bring a prosecution and perform retrospective analysis to understand what lessons can be learned is important. Attackers that reach this stage might start getting sloppy, and a large percentage of attacks studied to produce this Kill Chain were not detected until this point.
Findings – The Matrix
Our next step was to expand the Kill Chain, looking at each stage as a Tactic and accompanying these with their relevant attack Techniques. This brought us around to a final product in the form of a matrix, inspired by MITRE ATT&CK, which we believe provides an accessible entry point to our findings for security professionals who work with ATT&CK on a daily basis.
Download a pdf version of the Matrix here
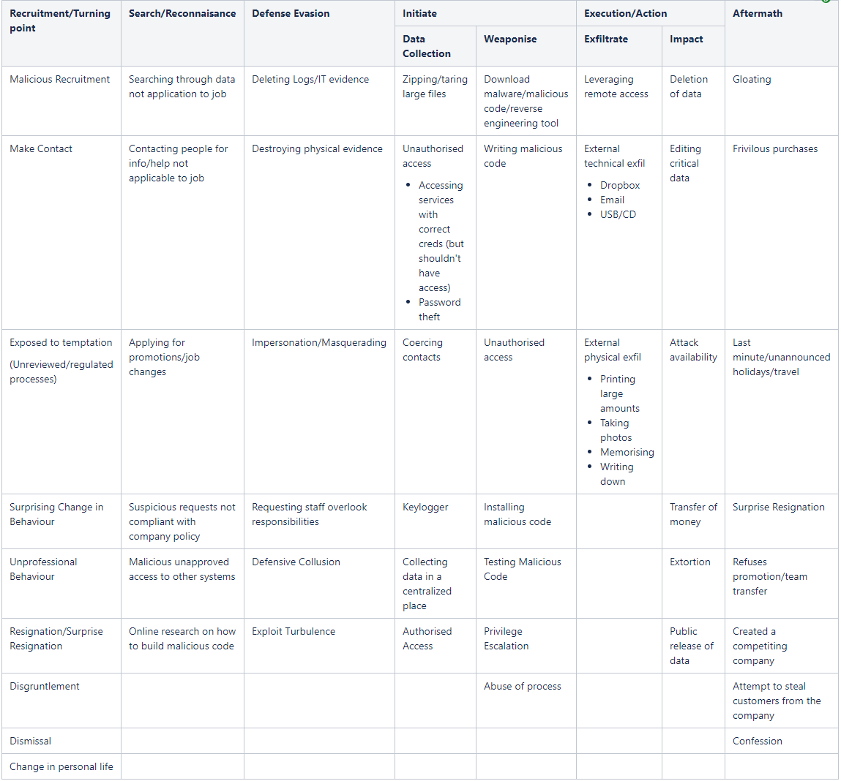
Figure 2: Insider Attack Matrix
How To Use Our Findings
Prevention
Having strong prevention, especially around operational controls and access control, goes a long way to helping protect yourself from external as well as insider threats. However good culture is also a great preventative control as well. Being able to identify strong points of contention within the company helps you remediate issues before they can become a turning point for a malicious insider. Additionally, a culture that helps people understand their security responsibilities helps make sure people don’t make mistakes that can be exploited by any attacker and also will mean people will enforce processes and not let colleagues cut corners, either for malicious reasons or out of pure unwillingness to follow process.
Detection
While lots of “external threat” detection controls help with insider threats, attackers often use legitimate access and processes to perform malicious activity. Attempting to create detections controls around these can produce too many false positives and may become unwieldy. There is also a wealth of data-feeds monitoring teams can depend on that help, specifically with insider threat. Examples include HR specific feeds, such as unannounced absence, promotion feeds and disciplinary feeds. Lastly, a strong culture around reporting near-miss events is needed as well. Human detection can identify and triage causes for concern much quicker than a Security Information and Event Management (SIEM).
Response
Identifying that an employee has performed an action linked to a technique in the matrix does not imply that the employee was doing something malicious. No technique is absolute. Often insiders use their own legitimate or approved access to perform something malicious. This means you cannot call in the cavalry because you have identified an employee performing one action detailed within the matrix. You need to correlate multiple attacks together to create a pattern of behaviour that can be construed as malicious. Even then, you shouldn’t react as if the employee is malicious. All this does, is warrant evidence that an investigation might need to be started
More Work Is Needed
We believe our framework gives security researchers, companies, governmental organizations – and anyone else interested in the problem – a good starting place for thinking about insider threat. And that is our intention that this work should serve as a starting point for the work of others. However, there’s always more research to put into the Insider Threat. Unfortunately, there’s no shortage of new cases coming to light on an ongoing basis. If you think you could help contribute please let us know – as we plan to expand the data feeds, and work on identifying the best prevent and detect capabilities for each technique.
Historians can argue about the defensive merits of Hadrian’s Wall for hours. Little is known about the Roman Legionnaires who constructed it, out at the edge of their known world. Were they contented? Did the wall make them feel safer from the Picts, the precursors to the todays’ Northeastern Scots? Probably. They kept it for 300 years.
But it’s worth realising that their feeling of safety may have been just that. A feeling. The biggest threat may have come from their own ranks. Our analysis can’t extend back nearly 1,900 years, but it’s easy to imagine disgruntled Legionnaires, 1,500 miles from Rome, at the edge of a failing empire, searching for some way to subvert their superiors – to try to stick it to the man, as only an insider can.
Contributors:
David Read
Ardavan Alamir
Simon Dugdale
Nick Stride
Dominic Lobo
